1. Managed DDoS Service
With the growing ubiquity of the “Internet of Things” that is being leveraged for creating new opportunities over the Internet, there is an increasing need for organizations to protect themselves from DDoS attacks as well as other constantly evolving, covert hacking techniques. Now more than ever, it is essential for organizations to maintain uptime of their vital business systems. And they need to do it without compromising the user experience for customers.
Clean Pipe to help protect against DDoS attack threats. Clean Pipe effectively protects against large L3-L4 DDoS attacks, which attempt to flood the core and downstream networks. Behind the mechanism is a comprehensive mitigation platform that inspects traffic, detects threats and blocks attacks against protected network resources, in real-time.
Clean Pipe not only provides improved bandwidth management, but also protects the connectivity and service of customer’s networks from the threat of evolving DDoS attacks, ensuring that first-rate network quality is always maintained for existing customers. It provides customers with the following benefits:
- Real-time network protection against DDoS attacks
- Provides individual IP address protection for mission-critical online services
- Consistent uptime connections and high, 24/7 availability
- Enables effective security cost management through real-time network insights
- Offers superior end-user experience
- Manages risk through optimized mitigation
The following proposal describes in detail the Clean Pipe offering:
- Clean Pipe Solution Overview
- Service Implementation
- Customer Requirements
- Service Management
Key Features
Key Benefits
Focus on your core business , leave DDoS protection to the experts.
- 100% availability, maintains user access to websites & applications.
- Flexible deployment profiles suit different deployment requirements.
- Enjoy unparalleled visibility of application traffic and threats in real time.
- SLA commitments with monthly performance review reports.
- Avoid negative publicity & customer churn.
- Attain regulatory compliance & avoid monetary
- Solid protection from DDoS attacks.
- Customizable granular profiles.
- Information on bandwidth usage
- Information on Top 10 visitors to your website
- Alerts to relevant information (detailed attack event playbacks for analysis.
- Real-time mitigation with customized Dashboard, view real-time traffic & attack events with periodic reports.
- Continuous development by Nexusguard against latest threats.
Features | Benefits |
Simple protection | • Providing peace of mind |
Granularity Profiles | • Suitable profiles for each network/host ip address • More effective on detection and mitigation |
Individual Dashboard | • Visibility of internet performance and usage • Two-factor authentication customer login portal • Data information |
Optional: Global Offload | • Easily upgradable for higher protection coverage • Auto cloud diversion |
Optional: CleanPipe + Application Protection (AP) + Origin Protection (OP) + DNS Protection (DP) | • Comprehensive protection from Layer 3 to 7 managed by Single Vendor |
Clean Pipe Solution Overview
Clean Pipe protects subnets transiting through the a network against DDoS attacks.
When a ddos attack is detected towards a host (/32), the mitigation platform will divert the /32 traffic over for scrubbing. After mitigation, clean traffic will be sent back to its destination. Clean Pipe Service is constructed from 4 key elements:
- Detection
- Mitigation
- Customer Portal
- Alert Notifications
The Mitigation Platform monitors and analyzes large pools of IPs in real time. Using behavioral or threshold based detection mechanisms, customers are notified of any occurence of abnormalities and attack events. The detection engine is a flow-based traffic analyzer and collector that supports NetFlow, SFlow, IPFIX and NetStream.
With a low false positive rate, the engine is capable of detecting a large variety of L3/4 attacks such as: TCP based data packets e.g. TCP SYN, TCP ACK, TCP RST, TCP Invalid, TCP Fragment; UDP based data packets e.g. DNS requests and responses, NTP data packets, SNMP data packets, SSDP data packets; ICMP based data packets e.g. ICMP Invalid, ICMP Fragment; IP based data packets e.g. IP Fragment, IP Bogons.
There are three modes of operation, Normal, Rapid and Smart.
Both Normal and Rapid Modes are based on thresholds. The detection engine calculates the traffic of each signature in real time and then compares them to a manually configured threshold. If the traffic signature is greater than that of the threshold, it will be treated as abnormal. The difference between the two methods lies in the time granularity; Normal Mode operates at the minute level, while Rapid Mode operates at the second level. The advantages of threshold based detection is that it is simple and easy to understand, control and implement and it is sensitive to traffic volume changes. However, the detection threshold of each signature needs to be manually configured and setting reasonable thresholds requires customer’s input.
Smart Mode uses machine learning algorithms to learn from historical netflow traffic data to detect whether the network is abnormal, i.e. under attack, and is automated to reduce customers’ manual configuration to a minimum. Rather than having to manually inspect large amounts of accumulated historical data, the Mitigation Platform harnesses and analyzes the data using Machine Learning models to help classify new incoming data or predict the next piece of data in a sequence. In the case of DDoS attack detection, the goal of the algorithm is to determine, on a scale of 0 to 1, how likely incoming traffic from a network is malicious. By analyzing masses of data, a well-trained learning model will be able to unravel convoluted characteristics of normal and malicious traffic that would have otherwise gone undetected to a human cybersecurity analyst.
The current Smart Mode detection process can be divided into two steps:
- A machine learning model detects the status of netflow traffic each minute. The status can be normal or abnormal.
- An attack event is generated according to the netflow traffic status each minute. At present, if the status is abnormal for three consecutive minutes, an event is started. If the status is normal for 10 consecutive minutes, the current event will end.
The advantages of Smart Mode is that it can automatically learn from large amounts of historical data and real time data, and customers do not need to perform much manual configuration when using this mode. It uses many traffic variables and it can identify more complex traffic patterns when compared to the threshold-based method.
Machine Learning models are very good at handling classification and predictive tasks, so long as the data is statistically similar to their learning models. But once they encounter new situations that vary from what they have previously learned, they can behave in unexpected ways. Although the use of Machine Learning to address the exponential threat of DDoS attacks is fast becoming a growing area of interest, it still requires a certain degree of human adjustment using supervised learning through network operators, but the overall results are very promising indeed.
Overall, three detection methods provide customers with options to deal with different types of requirements and traffic patterns. They can be applied to different profiles to provide the best result.
2.2 Mitigation
Upon activation, mitigation profiles will be applied to incoming traffic to mitigate attacks. Mitigation can be set hierarchically, allowing network operators to cascade mitigation filters for large networks and yet maintain the flexibility to define specific profiles for up to individual IP addresses. Multiple mitigation templates can be created with its own policies to be applied
quickly to a site or host IP.
A mitigation template is activated by default upon detection of threats. In other words, these rules are automatically enforced when the threshold values (e.g. upper limits) defined by detection policies are reached. The defense mechanism has an intelligent, built-in filtering system to identify and mitigate attacks while keeping the user experience intact. The filtering structure for the mitigation process is composed of the following:
- Blacklisting / Whitelisting
- Bogons
- Anti-flooding
- Flexfilter
- Zombie
- Traffic policing
To manage policies more effectively, mitigation profiles can be custom-defined at Site level and Host levels to suit your specific needs for general network protection and targeted application protection as illustrated in the diagram below:
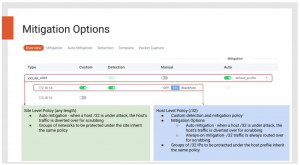
Figure 2: Site Level Policies Profile vs. Host Level Policies
2.3 Customer Portal
The Customer Portal allows customers to view the Clean Pipe configuration applied to the Mitigation Platform. On the Customer Portal, customers can monitor real-time traffic, ongoing and stopped DDoS attacks, and potential threats to an IP through a visually-pleasing interface. These essential analytics also translate into insightful business intelligence that allows the customers to understand the patterns of how your clients access and use your services. With a better understanding of their online behavior and favorites, you are in a better position to serve them and increase profit from existing clients, as well as pull in more targeted new customers.
The Clean Pipe service dashboard is organized to 3 main areas namely:
- Overview – the default page shown when the Clean Pipe service is selected. This contains the traffic information associated with the protected networks.
- DDOS Alert – this page contains all the important information related to the DDoS attack events and status.
- Top N – this page contains traffic profiles for baselining and shows the aggregate bandwidth usage, without distinguishing clean and attack traffic.
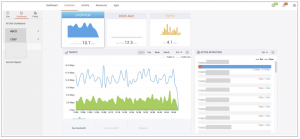
Figure 3: Customer Portal
2.4 Alerts and Notifications
The Event Notifier Application provides a centralized notification management for customers on CP DDoS attack event. Notifications can be delivered through Email/SNMP Trap/Syslog.
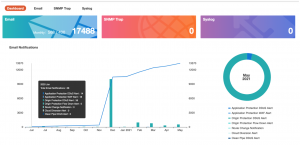
Figure 4: Event Notifier Application
Event Notifier allows customisation of alert level and time window for each event type. On Email notification, users can select the type of events that they want to receive.
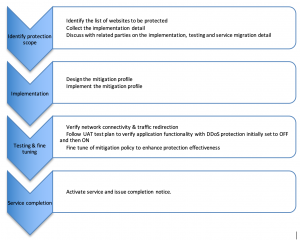
Figure 5: Alert Notification Options
3. Service Implementation
3.1 Implementation Plan
To facilitate the implementation process, a kickoff session will be arranged to share basic concept of DDoS, solution architecture, attack handling process as well as case studies in order to establish common understanding of the Mitigation Platform. It targets to any related departments such as Security, Infrastructure, Application, Development and including Service Team. It would be a good opportunity to build up client knowledge to familiarize the Clean Pipe service and different configurations to fit into client environments. The high level implementation plan is designed as follows:
Figure 6: Service Implementation Flow Diagram
3.2 Identify protection scope
The key part is to clearly identify the scope of protection and list out the resources for protection. With this protection list, we can start collecting the technical detail, understand the application logic and explore the normal application behavior as well as the protection scope.
As each application is unique in terms of traffic pattern and user behavior, our security specialist will need to discuss with the related parties before designing the optimal protection profile that can deliver a perfect balance between mitigation effectiveness and performance.
3.3 Implementation
With the scope of protection identified and technical requirements confirmed, designing and implementing the mitigation profile should be straight forward. An UAT plan is needed next to ensure all applications are functioning as designed no matter mitigation protection is enabled or disabled.
3.4 Testing & fine tuning
3.4.1 Network connectivity test
The network connectivity test should include test cases that involve all applications no matter if these applications require any layer of DDoS protection.
3.4.2 Functionality test
Functionality tests should focus on the application functionality based on the original UAT plan design for that application. This is then tested with DDoS protection initially set to OFF and then ON. The results are then compared to ensure consistent behavior and if fine tuning of mitigation policy is needed.
It would be ideal that an UAT platform can be arranged for functionality test. This has two advantages that the production services are not impacted.
3.5 High Level Provisioning Task
Task | Responsible party | Estimated duration |
Project kick off 1. Introduction of project team 2. Establish communication channel 3. Work out high level project plan & schedule | 1. CUSTOMER & VENDOR 2. CUSTOMER & VENDOR 3. CUSTOMER & VENDOR | 0.5 day |
Service scoping 1. Briefing of solution & implementation process 2. Confirm protection scope 3. Provide technical detail concerning network infrastructure, websites & domain names | 1. VENDOR 2. CUSTOMER & VENDOR 3. CUSTOMER | |
Mitigation profiling 1. Design protection profile 2. Implement protection profile | 1. VENDOR 2. VENDOR | 1-2 days |
Testing & fine tuning 1. Provide usual UAT test plan with test ID & data 2. Perform testing 3. Fine tune mitigation policy | 1. CUSTOMER 2. CUSTOMER 3. VENDOR | Estimate 1 week depending on the complexity of test plan |
Service completion 1. Issue completion certificate | 1. VENDOR | 1 day |
Table 1: High Level Provisioning Task
4. Customer Requirements
The DDoS protection requirements are summarized as follows:
Please specify the CIDR that require protection |
Attack coverage refers to the size of attack that you would like to be protected from |
Cleaned Bandwidth |
Table 2: Service Requirements
5. Service Management
We operate 3 tiers of 24×7 monitoring and local support, Network Security Analysis (NSA), Network Security Specialists (NSS) and SOC Managers, ensuring 7×24 all rounded support to customers.
Tier 1 (SOC-NSA) – The role of Tier 1 is to ensure that all Customer services are monitored from attacks, requests, enquiries and feedback are handled promptly as indicated based on our Service Level Agreement. Various communication channels namely live chat, email and hotline are utilized to facilitate efficient and convenient communication for customers to contact us during an incident.
Tier 2 (SOC-NSS) – Our Security Operations Center (SOC) is backed with Network Security Specialists (NSS), that are available 7 days a week on-call basis. Highly experienced and knowledgeable in the field of DDoS Mitigation, ensuring services of clients to be available.
Tier 3 (Deputy/SOC Manager) – Our Team is supported with Managers that are readily available to receive escalations from both internal and external clients. Any major event is overseen by our SOC Managers, and prepared to take over if needed.
6. Conclusion
Clean Pipe is designed to deliver a perfect balance of protection and network performance for customer’s Internet facing assets. It is delivered as a value-add on top of existing Internet connectivity to ensure uptime availability.

